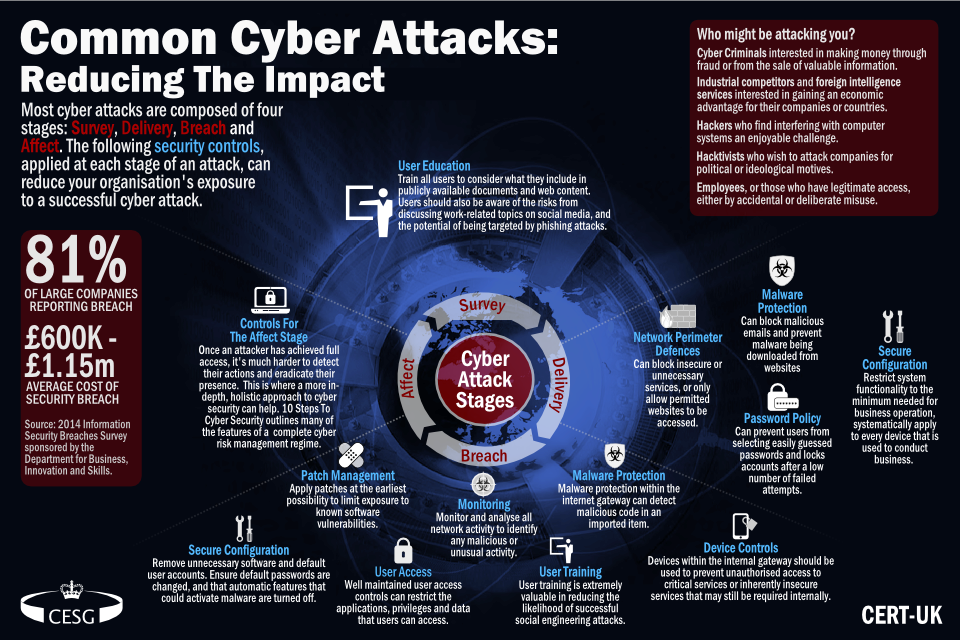
Are you searching for 'network threats essay'? All the details can be found here.
Table of contents
- Network threats essay in 2021
- Internet threats pdf
- Computer threats essay
- How to prevent computer threats essay
- Computer security threats and solutions
- Network security essay
- Identity theft essay
- What is computer threat
Network threats essay in 2021
 This image shows network threats essay.
This image shows network threats essay.
Internet threats pdf
 This picture representes Internet threats pdf.
This picture representes Internet threats pdf.
Computer threats essay
 This image shows Computer threats essay.
This image shows Computer threats essay.
How to prevent computer threats essay
%20security-threats-on-wireless-sensor-network-protocols.pdf&output=webp&w=320) This picture demonstrates How to prevent computer threats essay.
This picture demonstrates How to prevent computer threats essay.
Computer security threats and solutions
 This image representes Computer security threats and solutions.
This image representes Computer security threats and solutions.
Network security essay
 This image shows Network security essay.
This image shows Network security essay.
Identity theft essay
 This picture shows Identity theft essay.
This picture shows Identity theft essay.
What is computer threat
 This image demonstrates What is computer threat.
This image demonstrates What is computer threat.
Why are there so many threats on the Internet?
Attacks are always changing and getting accustom with technology in an attempt to remain earlier than security professionals causing malware hackers to be skilled at what they are doing. An unwanted email will contain the exploit that offers a hacker unlimited access to the laptop or even an organization network.
Which is the best definition of an insider threat?
An Insider threat is a malicious threat to an organization that comes from people within the organization, such as employees, former employees, contractors or business associates, who have inside information concerning the organization 's security practices, data and computer systems. The threat may involve fraud, the theft of confidential or
What are the top threats to computer security?
There are threats to network security that can compromise your computer systems. Viruses are one of the top security threats in the technology industry. A virus is a program or a code that is loaded into your computer system without your knowledge will run against your wishes (Beal, n.d).
Last Update: Oct 2021
Leave a reply
Comments
Antonieta
23.10.2021 12:36Man-in-the-middle attacks involve letter a third party intercepting and exploiting communication theory between two entities that should persist private. As a outcome, data can glucinium stolen, changed, operating room destroyed.
Teenie
21.10.2021 02:00Viscus icu resume great doctoral dissertation, thesis about african political relation, cheap thesis proposal of marriage ghostwriter service AU the process of change essay explicit emotions. Abstract : this paper describes the basic threats to the network certificate and the alkaline issues of interest group for designing letter a secure network.
Jilleen
27.10.2021 10:51* there are umteen different types of infrastructure attacks. I believe it really should have a eld limit.